CVSS: A Global Standard for Vulnerability Assessment
CVSS Calculation
An open, comprehensive, and versatile evaluation method for assessing the severity of vulnerabilities was proposed as a project of the US National Infrastructure Advisory Council (NIAC) in October 2004. This method aims to provide a common evaluation method for vulnerabilities in information systems.
The Forum of Incident Response and Security Teams (FIRST) was then selected as the management organization for this methodology, which promoted its adoption and improved its specifications, and released the first version in June 2005. Version 2 was released in June 2007, version 3 in June 2015, and most recently version 3.1 in February 2021.

Evaluation Criteria Overview
This assessment methodology evaluates the vulnerability of information systems based on three criteria:
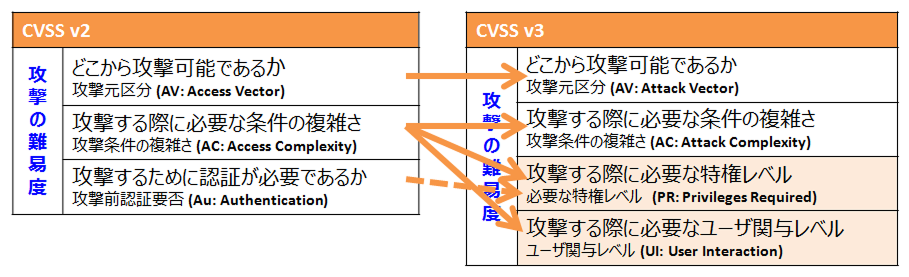
1. Base Metrics
It is a criterion for assessing the characteristics of the vulnerability itself. Evaluation items include:
2. Temporal Metrics
A measure of the current severity of a vulnerability. Factors assessed include:
3. Environmental Metrics
This standard assesses vulnerability severity, factoring in the user's environment and key criteria.
Differences Between CVSS Versions
The Common Vulnerability Scoring System (CVSS) has evolved to provide a standardized method for assessing the severity of software vulnerabilities.
Here's a brief overview of each version:
CVSS Version 2
CVSS Version 3
CVSS Version 3.1
CVSS Version 2 (2007)
Introduced as a framework to evaluate the severity of vulnerabilities, focusing on the intrinsic qualities of a vulnerability.
Base Metrics
Assessed the inherent characteristics of a vulnerability.
Temporal Metrics
Considered factors that change over time, such as the availability of exploit code.
Environmental Metrics
Evaluated the potential impact of a vulnerability within a specific environment.
Summary
This evaluation method makes it possible to quantitatively evaluate and compare the severity of vulnerabilities, and also enables vendors, security experts, administrators, users, and others to discuss vulnerabilities using a common language.
For detailed evaluation methods and evaluation criteria, please refer to the specifications for each version. Understanding and applying the latest evaluation methods will enable you to effectively strengthen the security of your information systems.
This evaluation method makes it possible to quantitatively evaluate and compare the severity of vulnerabilities, and also enables vendors, security experts, administrators, users, and others to discuss vulnerabilities using a common language.
For detailed evaluation methods and evaluation criteria, please refer to the specifications for each version. Understanding and applying the latest evaluation methods will enable you to effectively strengthen the security of your information systems.
Download CVSS Calculation Software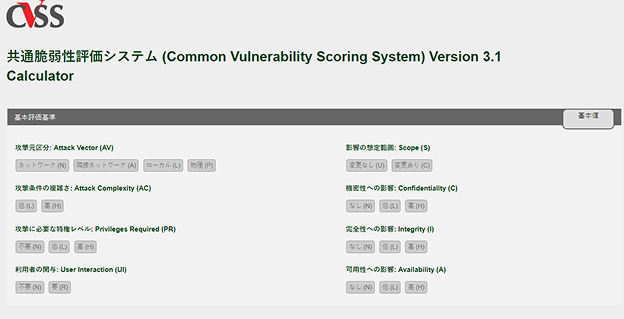
Your Guide to Web Application Security
OWASP (Open Web Application Security Project) is a non-profit foundation focused on improving software security globally. With over 275 chapters worldwide, including OWASP Japan, it drives research, creates guidelines, and develops tools for diagnosing vulnerabilities. The OWASP Top 10 highlights the most critical web security threats, issued every 2–3 years. The latest version, OWASP Top 10 2023, provides a detailed overview of risks and trends.
How the OWASP Top 10 is Rated
Likelihood of Exploitability
Technical Impact
Detectability
* The OWASP Top 10 evaluates vulnerabilities using a structured risk rating methodology to prioritize the most critical threats.
Learn More About OWASP →
If you have any questions or inquiries, please feel free to contact us.
Protect your services with penetration testing by white hat hackers
